IDA – Intimacy in Data-Driven Culture
1.6.2019 – 31.8.2025
Academy of Finland
Budget: 490 104 €

With the widespread use of digital devices, we have access to a wealth of information and several online services that largely replace the traditional way of conducting business onsite. However, this development has also brought about privacy concerns. Internet users’ personal information can be collected and used without their knowledge or consent. In today’s world, data collection has an increasingly important role when tracking and analyzing users’ daily activities. From purchased products to political opinions, data provides insights into every aspect of our lives. While this data can be used to create a convenient digital infrastructure that supports our daily routines, personal data often also ends up to third parties such as large analytics companies.
When third-party entities collect and process data, it can also be used for purposes that the individual did not consent to. This can include using personal data to create targeted advertising, or selling it to other companies. As few powerful companies or organizations gather large amounts of personal data, power imbalances are created.

The IDA project seeks to improve data privacy and data democracy – individuals should have the right to decide what personal data is collected about them, how it is used, and who has access to this data. The work packages develop experimental methods for studying data leakages and advance open privacy-preserving solutions for collecting, managing and using data.
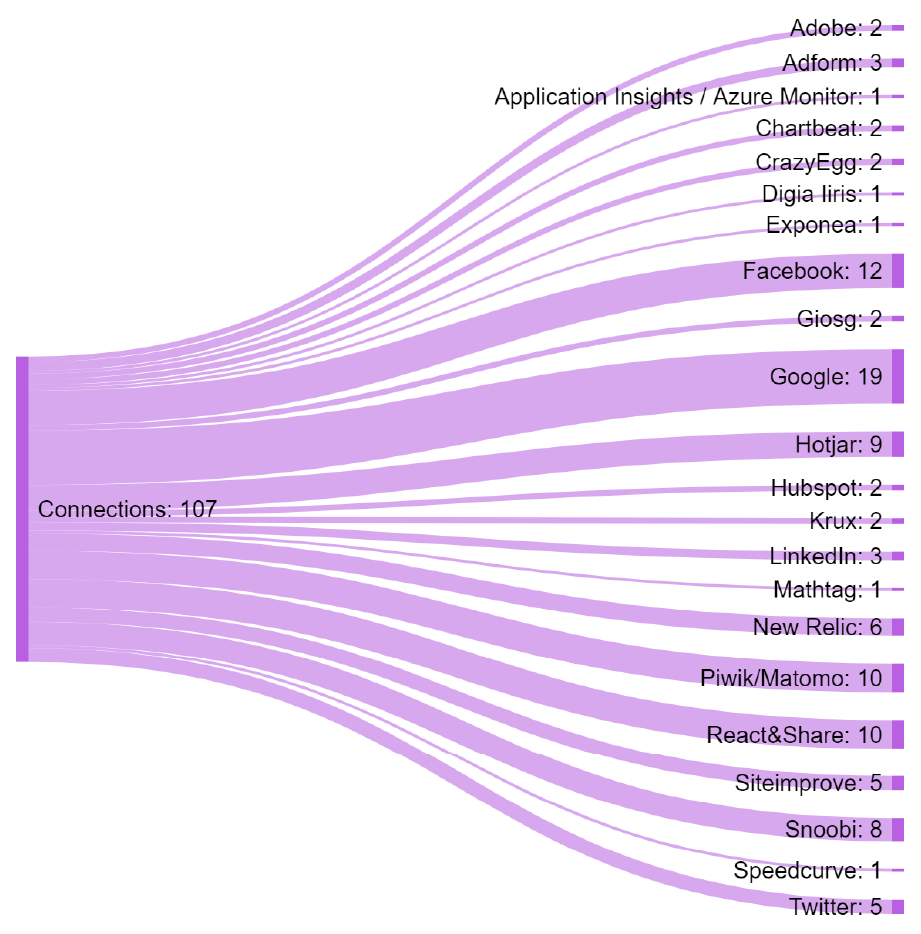
From the viewpoint of software engineering, the project studies privacy and third-party data leaks, especially in web and mobile environments. This includes, among other things, network traffic analysis, analyzing transparence of privacy policy documents, assessing properties of third-party analytics services, and finding methods to improve personal data protection in software development. The findings have revealed, for example, highly sensitive and intimate data leaks in Finnish online pharmacies, medical center websites, and voting advice applications.
Key Partners
- Aalto University
- Tampere University
- Faculty of Law, University of Turku
- Faculty of Humanities, University of Turku
Additional information
Ask more
Ville Leppänen
Professor
ville.leppanen@utu.fi
Phone +358 40 739 3060
Selected publications
Carlsson, R., Rauti, S., Laato, S., T., Heino, Leppänen, V. (2023): Privacy in Popular Children’s Mobile Applications: A Network Traffic Analysis. MIPRO 2023. Accepted, to be published.
Carlsson, R., Rauti, S., Mickelsson, S., Mäkilä, T., Heino, T., Pirjatanniemi, E., Leppänen, V. (2023): Several online pharmacies leak sensitive health data to third parties. Information Systems and Technologies: WorldCIST 2023. Accepted, to be published.
Ruohonen J., Hjerppe K.: “The GDPR Enforcement Fines at Glance”, Information Systems, 106: 101876 (2022), Elsevier. https://www.sciencedirect.com/science/article/pii/S0306437921001009?via%3Dihub
Heino, T., Carlsson, R., Rauti, S., Leppänen, V. (2022): Assessing discrepancies between network traffic and privacy policies of public sector web services. In Proceedings of the 17th International Conference on Availability, Reliability and Security (ARES ’22). Association for Computing Machinery, New York, NY, USA, Article 11, 1–6. https://doi.org/10.1145/3538969.3539003
Carlsson, R., Heino, T., Koivunen, L., Rauti, S., Leppänen, V. (2022): Where Does Your Data Go? Comparing Network Traffic and Privacy Policies of Public Sector Mobile Applications. In: Rocha, A., Adeli, H., Dzemyda, G., Moreira, F. (eds) Information Systems and Technologies. WorldCIST 2022. Lecture Notes in Networks and Systems, vol 468. Springer, Cham. https://doi.org/10.1007/978-3-031-04826-5_21
Hjerppe, K., Ruohonen, J., Leppänen, V. (2022): Extracting LPL privacy policy purposes from annotated web service source code. Softw Syst Model 22, 331–349. https://doi.org/10.1007/s10270-022-00998-y
Ruohonen J.: “The Treachery of Images in the Digital Sovereignty Debate”, Minds and Machines, 31(3): 439-456 (2021), Springer. https://link.springer.com/article/10.1007/s11023-021-09566-7
Ruohonen J., Tuikka A-M.: “Digital Divides and Online Media”, ICSET 2021: 2021 5th International Conference on E-Society, E-Education and E-Technology, pp. 157 – 163, 2021, ACM. https://dl.acm.org/doi/10.1145/3485768.3485815
Hjerppe K., Ruohonen J., Leppänen V (2020): “Annotation-based static analysis for personal data protection.” IFIP Advances in Information and Communication Technology. vol. 576.
http://dx.doi.org/10.1007/978-3-030-42504-3_22
Ruohonen, J., Hyrynsalmi, S., Leppänen V. (2020): “A Mixed Methods Probe into the Direct Disclosure of Software Vulnerabilities.” Computers in Human Behavior vol. 103. 161-173. https://doi.org/10.1016/j.chb.2019.09.028